Threat Intelligence
BianLian’s silent breach: How 1 exploit hit Nippon Steel’s supply chain
A deep dive into the Nippon Steel breach and BianLian’s growing focus on supply chain data theft. Learn how to defend your network.

Howard Poston,
Oct 28
2025
In early 2025, Nippon Steel Solutions uncovered an active breach on its network that targeted the sensitive information of its customers, employees, and partners. The previous month, ransomware group BianLian claimed responsibility for that breach and threatened to expose stolen data. While they are not proven to be behind the breach reported by Nippon Steel beyond that claim, the evidence suggests that this was solely a data breach without encryption—matching the group’s more recent tactics.
The Nippon Steel Solutions breach started life as a zero-day exploit, which expanded into a sophisticated attack that terminated in a likely data breach. In this Attack Anatomy piece, we’ll explore the incident in depth, mapping the tools and techniques most likely used by the attackers to the MITRE ATT&CK framework and Hack The Box resources.
By the end of this article, you’ll have everything you need to get hands-on experience with these types of threats and build better cyber resilience as a result.
Table of Contents
How the Nippon Steel breach (probably) happened
According to Nippon Steel’s official statement, the incident began with an exploit targeting a zero-day vulnerability in its network infrastructure. The end result of the incident was a breach exposing the information of the company’s employees, customers, and partners.
Publicly available sources don’t provide much information about this breach at the time of writing. However, knowledge of BianLian’s common tactics, techniques, and procedures (TTPs) can shed some light on what most likely happened. Let’s get into it.
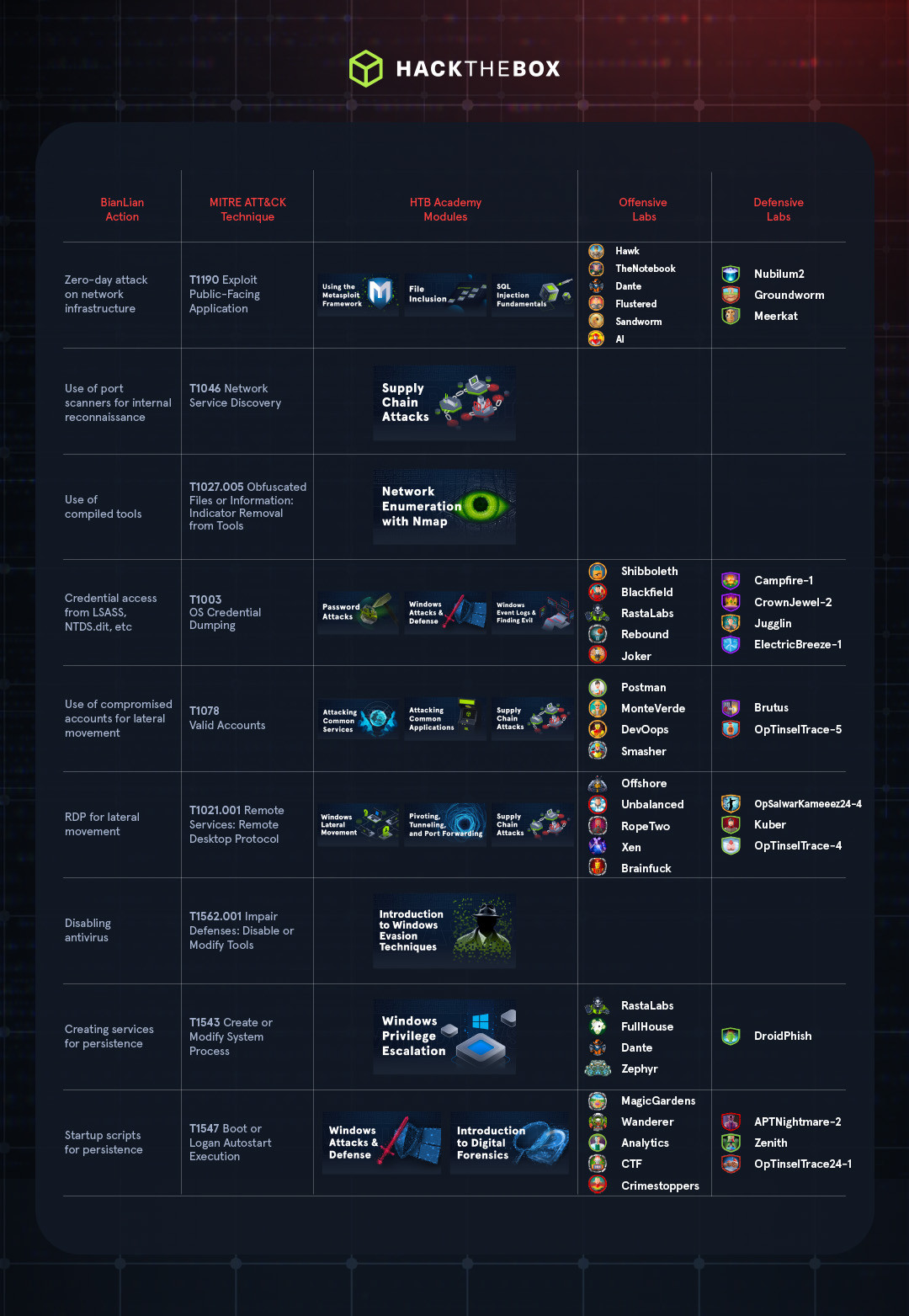
Initial access and lateral movement
TThe reported cause was an exploit of a zero-day vulnerability in a public-facing system (MITRE ATT&CK: Exploit Public-Facing Application). While the exact vulnerability wasn’t disclosed, it may have affected a firewall, VPN, or other remote-access service.
Once inside, BianLian typically performs extensive network reconnaissance, deploying tools like port scanners to map internal infrastructure (MITRE ATT&CK Network Service Discovery). These tools are delivered in a compiled form, which helps to evade signature-based detection (MITRE ATT&CK Obfuscated Files or Information: Indicator Removal from Tools).
While the exact vulnerability used wasn’t disclosed, this could indicate a vulnerability in a firewall, VPN server, or other public-facing system that could provide remote access to the organization’s internal network.
Be prepared for threats like BianLian
The APT also takes advantage of built-in Windows tools to collect legitimate credentials to use for lateral movement and privilege escalation. This includes looking for insecurely-stored credentials on compromised systems, dumping Local Security Authority Subsystem (LSASS) memory, and trying to access NTDS.dit for domain credentials (MITRE ATT&CK OS Credential Dumping).
With credentials in hand, they’ll use legitimate accounts and the the Remote Desktop Protocol (RDP) to move between systems in the compromised environment.
Defense evasion
The breach wasn’t detected right away. BianLian is notorious for disabling security tools and claimed to have breached Nippon Steel in March 2025, but the incident wasn’t reported until April. On top of that, the group behind the incident managed to access a wide range of sensitive information.
These two facts indicate that an attacker was likely present within the company’s network for some time, and BianLian is known for using various techniques to evade defenses. One of the most common is to actively target antivirus tools using PowerShell and Windows Command Shell (MITRE ATT&CK Impair Defenses: Disable or Modify Tools).
The likelihood of this occurring is reinforced by Nippon Steel’s statement, which included “advanced behavioral detection capabilities” as part of its remediation actions. This implies that additional controls were needed to identify the attacker beyond those already in place and that some existing systems may have been rendered non-functional.
It’s worth noting that BianLian’s practice of using built-in tools and “living off the land” is exactly what behavioral analysis is needed to detect, unlike common malware variants that could be identified by traditional AVs.
The group may have also implemented persistence mechanisms to prevent their access from being removed from compromised devices. This could involve creating services that are launched on system startup or user logon.
Data access and exfiltration
The Nippon Steel breach included unauthorized access and exfiltration of a significant amount of sensitive data. According to the official statement, the breached data included:
-
Name
-
Company name
-
Affiliation
-
Job title
-
Company address
-
Business email address
-
Telephone number
Based on BianLian’s TTPs, attackers likely identified and extracted specific data using stolen credentials and standard network tools. While the exact exfiltration method is unknown, cloud storage or command-and-control (C2) channels are probable. Nippon Steel’s “enhanced exit countermeasures” suggest that data exfiltration controls were added after the fact.
Protecting against similar attacks
While the exact details of the Nippon Steel breach are unknown, it’s far from an unusual story. Many organizations have been compromised and had sensitive data stolen via similar means.
Notably, the data stolen from Nippon Steel could enable phishing and social engineering against its business partners. Knowing who manages vendor relationships or approves payments offers a ready-made playbook for targeted fraud.
Defending against such attacks means detecting subtle activity, so:
-
Focus on behavioral detection for credential abuse and data movement.
-
Patch exposed services promptly.
-
Segment networks to limit lateral movement.
-
Train defenders to recognize adversarial behaviors through realistic simulation.
BianLian and other APTs are experts at flying under the radar, using various techniques to cover their tracks and reduce the likelihood of detection. Managing these threats requires understanding where to look for potential indicators of compromise (IoCs).
Hack The Box has a variety of resources designed to provide hands-on experience with the tactics and techniques used by BianLian and other threat actors. Familiarizing yourself with these techniques can help security teams to better design defenses and see the signs of attackers in their networks.
Editorial note: BianLian continues to focus on industrial and manufacturing targets, favoring data exfiltration and extortion without encryption. The group’s recent activity (September–October 2025) includes additional supply chain and logistics victims, confirming its shift toward intelligence-driven monetization rather than traditional ransomware.














