Cyber Teams
HTB Threat Range: See the next attack in action—and know exactly how your team performs
HTB Threat Range is a hands-on cyber defense arena where SOC analysts, DFIR investigators, and managers master detection, response, and reporting — boosting KPIs and team readiness.
Table of Contents
Threat actors are faster, stealthier, and more sophisticated than ever, often outpacing the defensive playbooks organizations rely on.
Security teams and leaders know this all too well. But the critical question remains: how confident are you in your SOC and DFIR teams’ ability to detect, respond to, and contain breaches in real time?
Too many organizations struggle to answer even the most basic readiness questions:
-
How fast is the SOC identifying real threats?
-
How often do false positives drain analyst time and energy?
-
How quickly are escalated tickets analyzed by DFIR?
-
How long do adversaries remain hidden in the network?
-
How much time is spent on investigations that yield nothing?
Every minute lost compounds financial, reputational, and regulatory risks. With AI-powered attackers moving faster, more efficiently, and with greater accuracy, those risks escalate even quicker, whether that’s through malware, ransomware, or social engineering at machine speed.
But, remarkably, these risks—along with team resilience—are rarely quantified. Most organizations still operate on assumptions, relying on playbooks and tools whose effectiveness hasn’t been stress-tested under real-world, AI-driven pressure.
What this means for your organization
Alert fatigue has become endemic, with 71% of analysts reporting burnout from overwhelming noise. Detection of major incidents still takes hours and sometimes days while adversaries often remain hidden in environments for a week or longer.
It’s now a well-known fact that skill gaps within teams triple the average time to respond, giving attackers extended windows to escalate privileges, exfiltrate data, or deploy ransomware. And the financial toll is heavy: organizations facing delayed detection incur average costs of $3.5 million in fines and reputational damage.
The missing link here is clear. Most security programs, despite engaging in some form of upskilling, lack the ability to measure, benchmark, and continuously improve team readiness against emerging threats or adversary groups.
Enter HTB Threat Range
HTB Threat Range is a live-fire, team-based simulation that tests SOC and DFIR squads under realistic cyber attack scenarios.
Part of our existing CTF platform, this new mode stress tests teams ability to handle attacks real-time, instantly validating team’s mission readiness and skills gaps. It combines the realism of a live cyber incident with the safety of a sandboxed environment, giving SOC and DFIR teams the chance to operate as they would in a real breach, only with measurable outcomes.
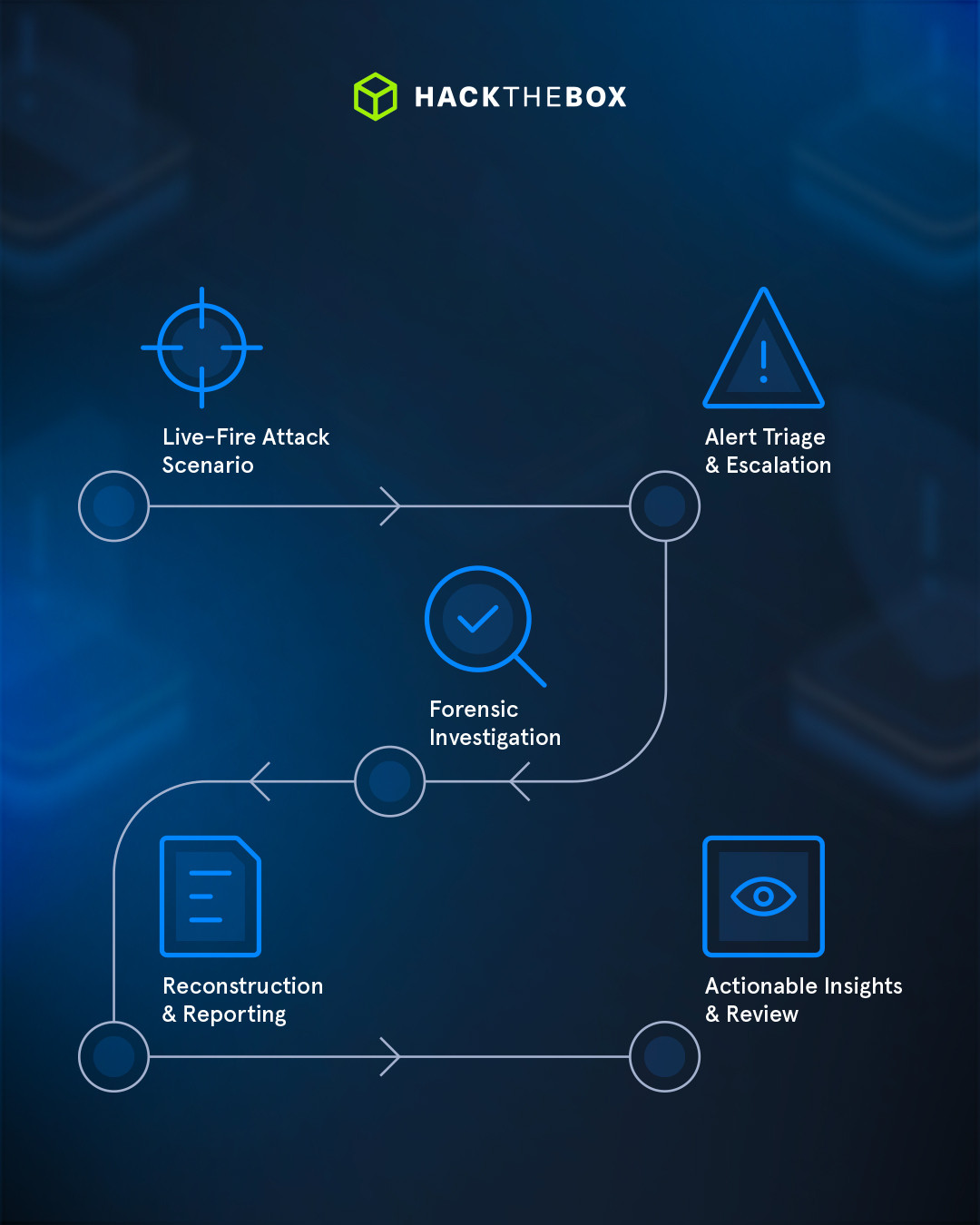
The gameplay: How Threat Range works
Threat Range is structured around the full incident response lifecycle, divided into clear phases that mirror the roles of real defenders in a safe, sandboxed environment.
1. SOC Analysts: First line of defense
Analysts start with a queue of alerts in a SIEM. Each alert must be triaged: discarded as noise or escalated as a genuine threat.
Analysts must document their rationale for every decision, honing judgment and accountability. This phase ensures teams practice prioritization under pressure and produces metrics on detection speed, accuracy, and false-positive rates.
2. DFIR teams: Investigating the attack
Escalated alerts are handed to the DFIR team, who dive into forensic artifacts to trace lateral movement, privilege escalation, and exfiltration attempts.
Using these findings, they reconstruct the full attack kill chain. Every step is tracked and scored, giving leaders actionable insight into investigative workflows and skill gaps.
3. Incident Response leaders: Containment
IR managers oversee the simulation, making high-level decisions about containment, mitigation, and playbook adherence. Their role is to ensure team coordination and decision-making under pressure rather than analyzing every artifact themselves, giving them real-time visibility into operational readiness.
4. Managers and executives: Full performance visibility
While analysts and responders work through the attack, managers and executives monitor the operation, observing:
-
How quickly alerts are handled
-
How effectively teams collaborate
-
Where systemic gaps emerge
5. Final Stage: Assembling the evidence
Once the attack is contained, the team collaborates to produce a comprehensive forensic report. They reconstruct the adversary’s behavior, timeline, and objectives using evidence collected throughout the simulation. The report can be iteratively refined over a five-day window, capturing lessons as they emerge.
Collaboration is crucial. Analysts, responders, and investigators operate side by side rather than passing incidents through silos. Every action is tracked, scored, and converted into measurable metrics, feeding directly into the Threat Resilience Index (TRI) for benchmarking team performance.
The Threat Resilience Index: Measuring what matters
At the heart of Threat Range is the Threat Resilience Index (TRI), a dynamic scoring mechanism that quantifies how effectively a team detects, triages, escalates, and resolves threats throughout an exercise.
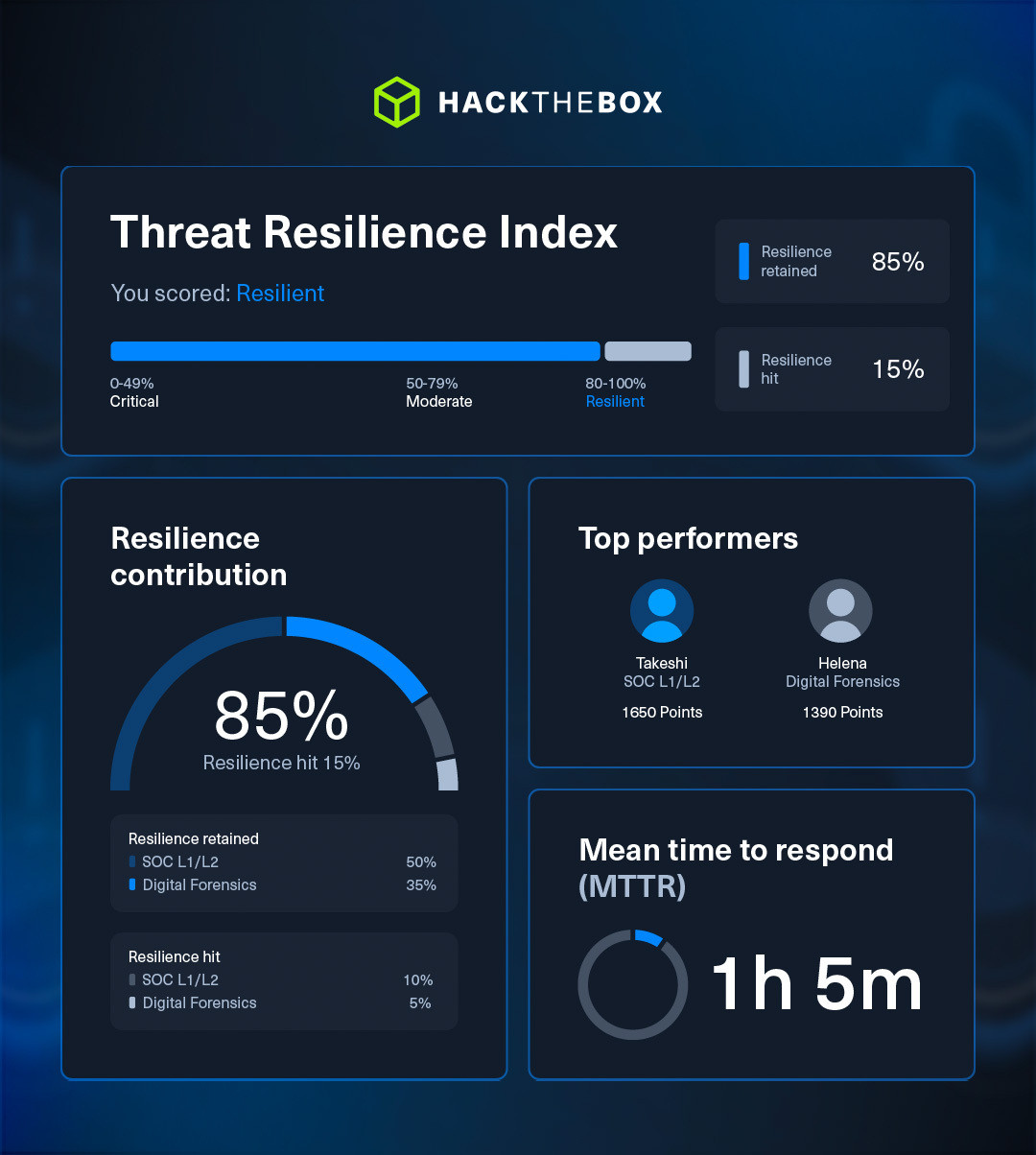
It is not a vanity metric. It simulates and quantifies an organization’s resilience under actionable metrics and player’s performance. This is a metric that players can experience in the entirety of the event as they manage to properly escalate threats and adhere to SLAs.
By running multiple scenarios, security leaders can observe improvement over time, compare performance across teams, and create a cycle of measurable growth, turning team development into a strategic advantage.
For executives, the Threat Resilience Index provides something invaluable: clarity. It transforms abstract questions of readiness into concrete evidence, empowering decision-making about staffing, tooling, and process investments with data.
Advanced reporting and board-ready insights
Threat Range doesn’t just test your team—it measures them with surgical precision. Every simulation is converted into a rich performance report that drills down into the metrics that matter most for SOC, DFIR, and leadership alike. This includes:
-
Threat Resilience Index (TRI): A holistic score of team readiness across the entire kill chain.
-
MTTA, MTTD, MTTI, MTTR: Time-bound metrics that expose exactly how fast your team acknowledges, detects, investigates, and responds.
-
True/False positive accuracy: A real measure of judgment under fire—no more hand-waving over alert fatigue.
-
SLA adherence: Proof of whether your team can perform under pressure and within business-critical thresholds.
And here’s the cherry on top: an AI-powered evaluation engine. Instead of asking for canned, exact phrasing to validate an analyst’s or responder’s work, Threat Range uses natural-language recognition to assess intent and accuracy.
That means your team gets judged on what they do and discover, not how they explain it. The result? A way more realistic, fair, and scalable performance assessment.
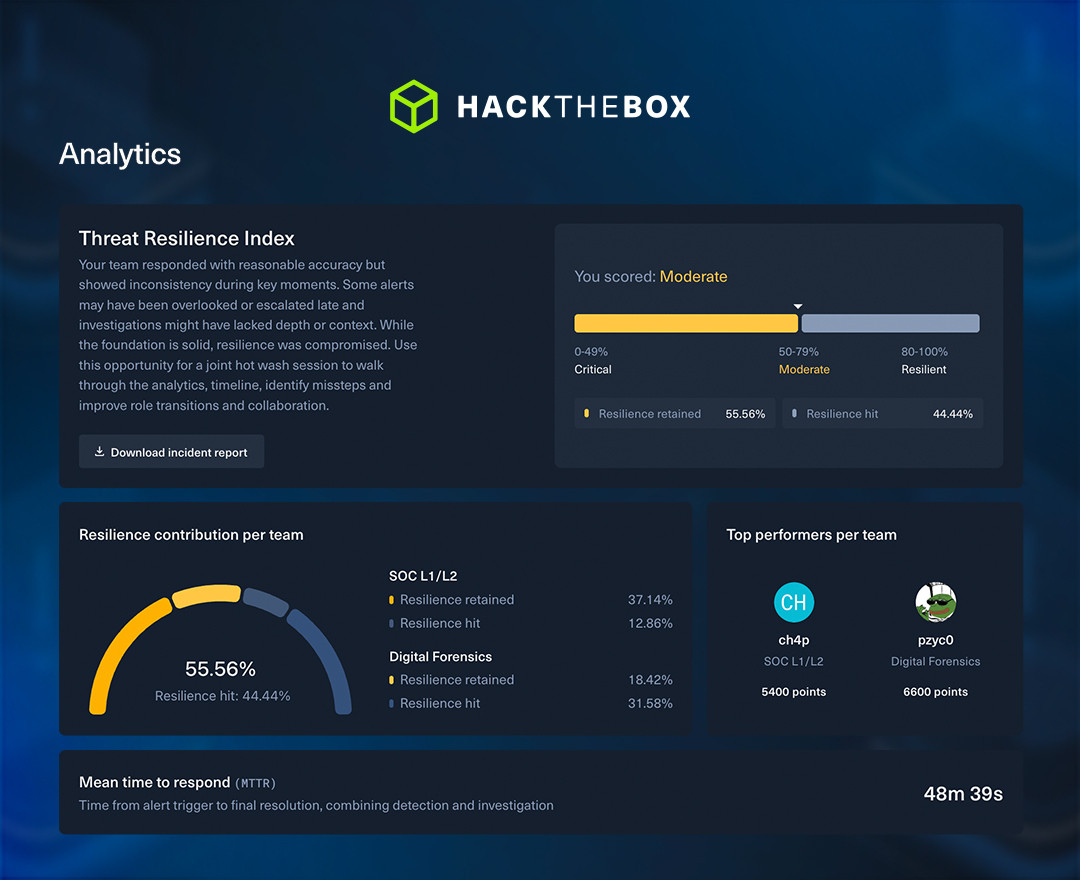
This level of analysis is unprecedented. Other platforms might stop at “did they catch that alert?” But Threat Range goes way beyond that, reconstructing the full investigative narrative, comparing your forensic report to the actual attack storyline, and surfacing where the team nailed it and where they missed critical steps.
For leadership, this translates into insights with bite:
-
SOC managers can pinpoint exactly where false positives drain capacity.
-
DFIR leads can see which workflows crack under pressure.
-
CISOs get the hard evidence boards and regulators demand—proof of resilience, readiness, and ROI on security investments.
No assumptions, no vague dashboards. Just hard, relevant data that transforms incident response performance from a guessing game into a measurable, improvable discipline.
“Threat Range was great. I really liked the realistic scenario it mimicked; it actually helped create a team responsible for responding to incidents in an organization. You saw the mix of Level 1 and Level 2 SOC teams collaborating to solve and address the incidents that occurred with a forensics team.” — Marbin Pazos Revilla, Assistant Professor of Instruction and USF CyberHerd Coach @ University of South Florida.
How you can use Threat Range
The greatest value of Threat Range is its versatility. It isn’t just about practice—it’s about giving teams the right environment to test, prove, and improve their readiness under real-world conditions. Here are three ways organizations can put Threat Range to work:
-
Run live-fire drills to validate readiness: Simulate advanced cyberattacks in a safe, controlled environment. Teams gain real-time experience detecting, escalating, investigating, and responding—while leaders get a clear picture of performance across critical KPIs like detection speed, investigation accuracy, and SLA adherence.
-
Test defensive playbooks and tooling under pressure: Stress-test SOC and DFIR workflows, escalation paths, and security controls against realistic, AI-driven attack scenarios. This allows leaders to uncover systemic weaknesses early, refine processes, and prove whether current investments are truly effective.
-
Benchmark performance across teams and shifts: Compare how different SOC shifts, business units, or geographies perform on a standardized scale. Threat Range brings consistency and fairness to measurement, enabling large enterprises to scale resilience and track measurable improvements over time.
With data-driven evidence of workforce readiness and resilience, CISOs and executives can confidently validate current investments, justify new initiatives, and demonstrate measurable progress to boards and regulators. In an industry where accountability is critical, Threat Range provides the clarity leaders need to strategically manage cyber risk.
“[Threat Range] brought different disciplines together and that mimics the reality of responding to cyber incidents in any organization.” —Marbin Pazos Revilla, Assistant Professor of Instruction and USF CyberHerd Coach @ University of South Florida
The report card every CISO wants to see
Cyber incidents won’t stop, but with Threat Range you won’t have to wonder if your team is ready. Every scenario delivers hard data, from the Threat Resilience Index (TRI) to MTTA, MTTD, MTTI, and MTTR, plus accuracy scores on detection and SLA adherence.
AI-powered evaluation ensures responses are validated in context, not just by keywords, so your SOC and DFIR teams are measured on what really matters: their ability to detect, investigate, and respond under intense pressure.
The result? Actionable, boardroom-ready reports that benchmark performance, spotlight skill gaps, and prove resilience to stakeholders.
Equip your defenders with the right environment to practise, compete, and grow—before the next threat hits. Threat Range is available as an add-on for all business plans.
















